Can invoice fraud be stopped?

How Invoice Fraud Works and How to Prevent It?
Between 2013 and 2015 a scammer based in Lithuania sent fake invoices worth over $100 million to Google and Facebook while masquerading as a Taiwanese supplier. The fake invoices passed the internal control measures at each company and were paid, over and over for years. How could this have happened to two of the most sophisticated companies in the world, and how can it be prevented?
The invoice fraud explained
Fake invoices cause billions of dollars in losses per year. Here is how they work…
A scammer becomes aware of the business relationship between two companies and sends the payer (let’s call them BIGTECH) an invoice pretending to be the payee (let’s call them SUPPLIER). The bank account listed in the fake invoice is the scammer’s.
A simple scam is to send an invoice to BIGTECH from a spoofed e-mail address like dan@SSUPPLIER.com instead of dan@SUPPLIER.com. A more sophisticated scam is to hack into SUPPLIER.com to send the invoice directly from dan@SUPPLIER.com. This latter form of invoice fraud is called business email compromise, or BEC.
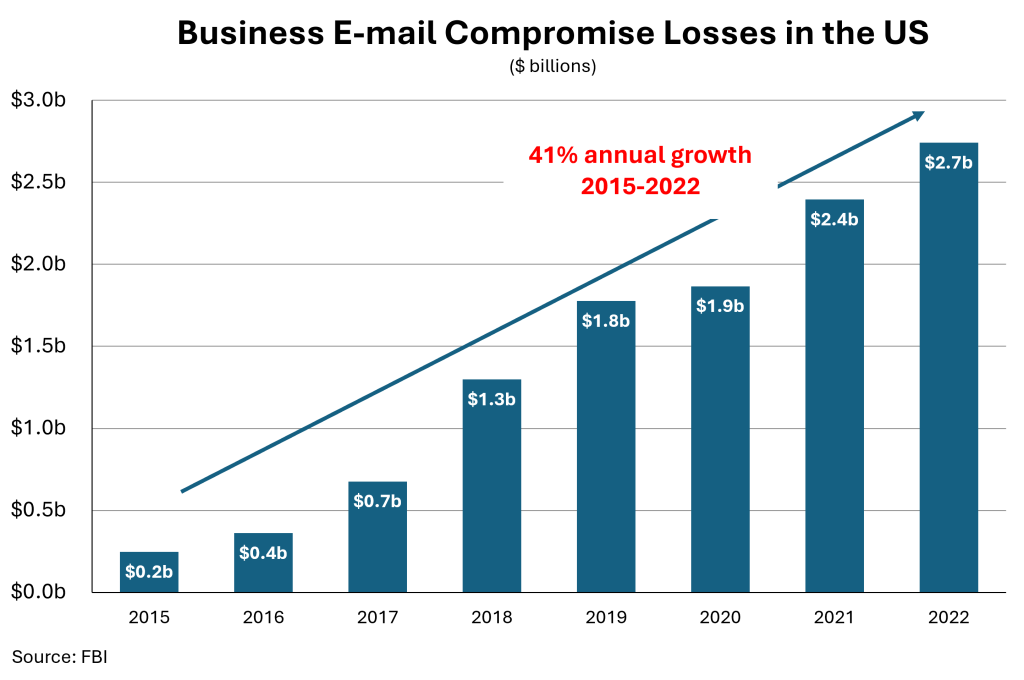
If BIGTECH falls for the scam both companies lose. SUPPLIER supplies the products but does not receive payment. BIGTECH sends the money to the wrong place and retains its payment obligation. A he-said she-said sometimes ensues.
Call-backs: the world’s most popular invoice fraud prevention measure
The standard approach suggested by banks, insurance providers and common sense to prevent invoice fraud is call-backs.
BIGTECH, upon receiving the invoice, calls a representative of SUPPLIER to confirm the payment details on the invoice. Once SUPPLIER confirms their bank details by phone, the invoice is paid.
If the right person is called, then indeed this approach avoids most invoice fraud. However, call-backs require time and effort for both companies and are thus costly. A successful call-back requires coordination or, likely, multiple tries to reach the right person at SUPPLIER. Furthermore, coordinating the call-back cannot generally be done over e-mail, since the scammer potentially controlling the e-mail address is the underlying problem.
Because a call-back is costly and additionally because some payments come with urgency, a call-back is often not performed as diligently as is needed for it to be an effective control measure. Moreover, since phone calls are analog in nature, it is difficult to create a record of whether a callback happened and whether the conversation properly confirmed the relevant payment details. In the case of a dispute between BIGTECH and SUPPLIER, this lack of record can become very costly.
A cryptographic solution to invoice fraud
An effective solution for invoice fraud must give an invoice more than one factor of authentication, such that if one factor (like an e-mail address) is compromised, a false invoice will still show as invalid. Most invoice fraud solutions that we’re aware of, whether call-backs or digital, create some additional factor(s) of authentication.
An ideal second factor is simple to attach and universally verifiable. Digital signatures are a promising solution but a verification process based on standard digital signatures is difficult to scale across a very broad set of global organizations that use a wide variety of software.
A vBase Stamp allows a digital signature to live external to the invoice itself. It is thus a form of universally verifiable digital signature. Once SUPPLIER vBase Stamps his invoice. BIGTECH can verify its authenticity via tools.vbase.com/verify (or any interoperable service) on any device that has access to the internet.
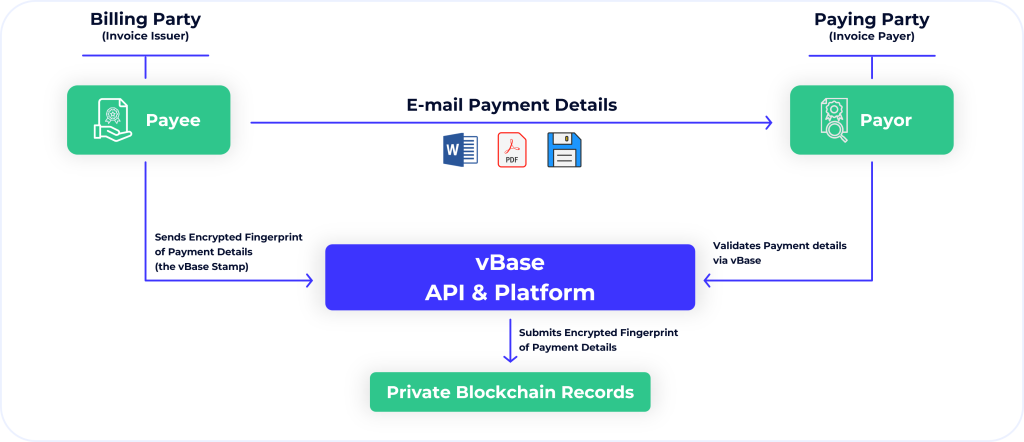
In comparison to call-backs the vBase verification process takes seconds to complete and can be automated entirely. Crucially, the vBase process does not require reaching a live person by phone, and can create an auditable record of whether the invoice verification took place.
SUPPLIER stamps and sends the invoice and never looks back. BIGTECH verifies the stamp and has peace of mind. The scammer is out of business.
Want to learn more?
The vBase web platform and open API allow anyone to start stamping their digital documents and data, creating easily verifiable information about authenticity and provenance.
Contact hello@vbase.com for more information
Recent Posts
 Why Great Returns Don’t Attract Investors
Why Great Returns Don’t Attract Investors
Many investors are unable to convert strong returns into clients or capital. Learn why and how to fix it.
 Mitigating BorgBackup Client Compromise
Mitigating BorgBackup Client Compromise
A compromised BorgBackup client allows undetectable tampering with past backups. vBase offers a simple solution.
 Stop Using Brokerage Statements to Show Your Track Record
Stop Using Brokerage Statements to Show Your Track Record
Many traders use brokerage statements to create a verifiable track record. Unfortunately they are not credible for this purpose. A better alternative exists.